Mobile Digital Banking Cyber Security is now a highly topical. As Banks give customers greater choice and independence to do their banking via mobile and digital channels, so ‘bad actors’ acquire exponentially greater opportunities to find and exploit weaknesses and gaps. That’s because the risk that ‘bad actors’ will find the dark ‘back-alleys’ and murky back-doors of bank systems.
The issue of Cyber-security threats to banking in 2023 has become so serious that the Australian Fintech institute has rated CyberSecurity in Banking among its top risk this year.
And this is when the Cybersecurity Risk and Attacks are greatest because any breach in Banking System Security also comes with devastating consequences.
That’s why Banking cybersecurity Security professionals need to stay one step ahead in the cat-and-mouse game of securing the bank and their customers against bad actors and malfeasance, and alert to new threats and attacks.
Mounting a coherent response means taking a wholistic view of both systemic and non-systemic issues where banking cyber-experts focus their energy into two broad streams or vectors; namely “Risk vectors” and “Attack vectors”.
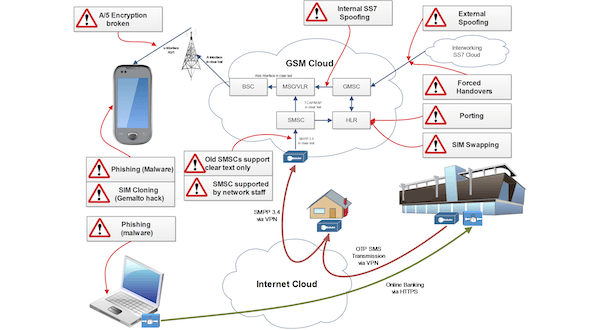
ATTACK VECTORS
Cyber Security Mobile Digital Risk and Attack Vectors: What’s the difference?
Both Risk and Attack vector response strategies have the same goal, namely identifying and assessing potential threats before they become a problem – but each has somewhat different ways of going about this.
Cyber Security Mobile Digital Risk Vectors explained
Typically Risk Vectors encompasses the different factors that contribute to the overall risk profile and landscape of the organisation or system they are trying to protect.
The term ‘Risk Vector’ refers to those technical and non-technical elements that, in combination, increase the likelihood of a successful attack or the potential impact of an attack. So, for example a weak risk culture, combined with a laissez faire approach to vendor management and a high turn-over of skilled staff, combined will act to increase the ‘Risk Vector’ rating. So in this example there may be no specific technical issue that creates a vulnerability, these factors combined may increase the odds that of a weakness that hackers may exploit. And so the term ‘Risk vectors’ take into account both Technical and Non-technical aspects, including:
Vulnerabilities: Weaknesses or flaws in systems, networks, or applications that can be exploited by attackers.
Threat Actors: Individuals or groups with malicious intent, such as hackers, cybercriminals, or insiders, who pose risks to an organisations security.
System Configurations: Inadequate security configurations or misconfigurations that increase the likelihood of successful attacks.
Data Sensitivity: The value and sensitivity of the data held by an organisation, which may make it an attractive target for attackers.
Regulatory Compliance: Adherence to legal and industry-specific regulations to ensure protection of sensitive information and avoid penalties.
So, Risk vectors focus on assessing the overall risk posture by considering vulnerabilities, threats, data sensitivity, regulatory requirements, and other factors that can influence the likelihood and impact of a successful attack.
Cyber Security Mobile Digital Attack Vectors explained
Attack vectors on the other hand, generally makes reference to the specific method or path that cyber attackers use to gain unauthorised access to a system or exploit vulnerabilities. Attack vectors describe the technical ways hackers carry out attacks.
Malware: Attackers may use malicious software like viruses, worms, Trojans, or ransomware to compromise systems.
Social Engineering: Hackers use phishing, pretexting, or baiting to trick individuals into revealing sensitive information or performing actions
Network Exploits: Attackers exploit vulnerabilities in networks, protocols, or applications to gain unauthorised access, execute malicious code, or manipulate data.
Physical Attacks: Physical access to hardware, devices, or infrastructure compromise systems or steal sensitive information.
Web-Based Attacks: Web-based vectors include cross-site scripting (XSS), SQL injection, or distributed denial-of-service (DDoS) attacks targeting web applications and services or other types of intrusion techniques.
Mobile Digital Banking Cyber Security Vector Summary
In Summary, “Attack vectors” breach security defences and gain unauthorised access, disrupt services, or steal information.
By paying attention to both Risk and Attack vectors, means the cyber-security guardians now have a strategy that encompasses both the techniques employed by attackers to breach security defences, and a broader range of factors, such as culture or behaviours, that together contribute to the overall risk landscape, and includes all potential ways that vulnerabilities and threats may materialise.
Bank IT system security professionals who aspire to excel in their roles, stay updated with industry trends, and ensure the robustness of mobile banking systems should not miss this course. Join us and embark on a transformative learning journey here at the CybersecurityX course.
Where to start your Mobile Digital Banking Cyber Security response
The cybsersecurity-x: safeguarding mobile & digital financial transactions Training Course is a comprehensive program designed for Banking professionals aiming to enhance their expertise in safeguarding mobile banking transaction security, from application designers and software developers to cyber-security professionals. This course spans 10 modules, covering key issues in mobile and digital banking security; from bank vulnerabilities, browser exploits and mobile device risks to external threats such as GSM/LTE network vulnerabilities and how to deal with network intrusions.
By attending this Training, delegates gain a comprehensive understanding of the challenges and best practices in securing mobile banking systems, equipped with practical skills to identify vulnerabilities, implement security measures, and promote a secure and trusted mobile banking environment. Delegates will have the opportunity to enhance their professional profiles, contribute to organizational security, and increase customer confidence in mobile banking services.
Get in Touch today!